Friends, the MidnightDBAs have a plan for 2022. A capital-P Plan. And it involves writing and teaching a lot.
The plan for January 2022 is a focus on SQL Server security. We’ve already collaborated and published one blog over at MinionWare.net: UNDERSTANDING SQL SERVER SECURITY: Secure xp_cmdshell with the Microsoft Master’s guide (in 4 not-so-easy steps).
It’s a long title. Things on the internet apparently adore long titles.
AND! AND! We have a live event on security coming up this week, Thursday January 20.
First, the “Secure xp_cmdshell” article
This is the xp_cmdshell security guide that I always wanted and could never find, so I wrote it. I encourage you to go read through it, but here’s the executive summary:
When we look to lock down xp_cmdshell, our primary goal must be to prevent SQL from becoming a conduit for mucking up the operating system…and files, and network, and other servers in the domain, etc.
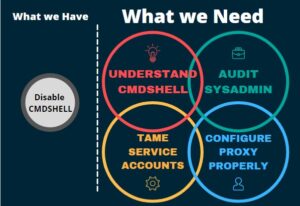
The four key areas to securing cmdshell are:
- Sysadmin
- Service Accounts
- MSDB Rights
- Minimum rights for the cmdshell proxy (if any)
Like I said, that’s just the summary. You really should go read the whole article.
Next, the security live event on LinkedIn Live
On Thursday, January 20 Sean and I are presenting “Learn SQL Server Security: xp_cmdshell edition” on LinkedIn Live!
That link you just read past? Click it and register, pretty please. It’s going to be a good time. What’s more, I made a bet on Twitter that we can teach you at least ONE thing about cmdshell security that you didn’t know before. Learning AND gambling*, what fun!

That’s all for today. Make sure you sign up for Thursday’s event!
Cheers,
Jen
*It’s not real gambling, Government Entities. Just a turn of phrase. Don’t raid us or anything.